Talk:Computer security
| This is the talk page for discussing improvements to the Computer security article. This is not a forum for general discussion of the article's subject. |
Article policies
|
| Find sources: Google (books · news · scholar · free images · WP refs) · FENS · JSTOR · TWL |
| Archives: 1, 2, 3Auto-archiving period: 365 days |
| Computer security is a former featured article. Please see the links under Article milestones below for its original nomination page (for older articles, check the nomination archive) and why it was removed. | ||||||||||||||||
| ||||||||||||||||
| Current status: Former featured article | ||||||||||||||||
| This It is of interest to the following WikiProjects: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| The contents of the Digital security page were merged into Computer security on 1 May 2023. For the contribution history and old versions of the redirected page, please see its history; for the discussion at that location, see its talk page. |
| The contents of the Computer insecurity page were merged into Computer security on March 16, 2014. For the contribution history and old versions of the redirected page, please see its history; for the discussion at that location, see its talk page. |
| On 4 July 2023, it was proposed that this article be moved to Cybersecurity. The result of the discussion was not moved. |
| The Cybersecurity article was blanked and that title now redirects to Computer security. The contents of the former article are available in the redirect's history. |
|
This page has archives. Sections older than 365 days may be automatically archived by Lowercase sigmabot III when more than 5 sections are present. |
Article Cleanup
[edit]I am planning on fixing grammar and style issues and cleaning up the article in general. If you disagree with with any of the content removal, please let me know. Thanks. — Preceding unsigned comment added by 208.250.65.158 (talk • contribs) 13:13, July 17, 2007 (UTC)
Can you be more specific about changes Tonymetz 💬 16:36, 1 April 2024 (UTC)
- That's an IP post from 17 years ago... i just added a sig so it will archive. Meters (talk) 20:23, 1 April 2024 (UTC)
Create new article for cybersecurity
[edit]I suggest creating a new article to separate cybersecurity form computer security, the justification and explanation of why it is different is in the suggested article: https://en.wikipedia.org/wiki/Draft:Cybersecurity
But in summary, both concepts can be improved having separate articles for Computer Security and cybersecurity, because cybersecurity includes the protection of elements and processes which are not technology but depend on technology, as society depends more and more on technology. Pcoronaf (talk) 22:11, 14 November 2023 (UTC)
article proposal
|
|---|
Proposal[edit]Cybersecurity should be differentiated from other types of computer security and information security, covering not only the protection of information but the infrastructure, services and supply chains dependent on information technology and communication systems. CISA defines it as the "art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information." [1] Cybersecurity is defined by NIST as "Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation."[2] 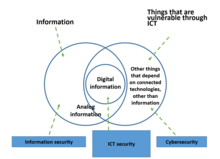 The increasing use of information technologies in an increasing number of applications, not only for data or information management, but to support, automate and efficient work and activities of all kinds, applied to all productive, entertainment and personal use sectors has led to an exponential growth in the number of connected devices. In this way we find connected devices for the control and automation of home functions - called home automation - such as on and off lights, climate control and air conditioning, opening and closing doors, among others. In the same way in the business environment we find devices that control alarms, elevators, fire monitoring and control, room automation, access control of staff and visitors, and many other applications. Connected cars, medical devices – including some inserted into the patient body, such as pacemakers and insulin pumps – are increasingly coming to market, industrial controls, power, gas and other basic supplies. It is related to information security and computer security, but also considers the protection of related infrastructure, products and services. Then cybersecurity is the protection of information and telecommunication technologies (ICT), the data processed and the infrastructure, products and services depending on them. [3] The Information Systems Audit and Control Association (ISACA) defines cybersecurity as "the protection of information assets by addressing threats to information processed, stored, and transported by internet worked information systems"[4] Pcoronaf (talk) 17:15, 25 May 2022 (UTC) International[edit] The International Telecommunication Union publishes the Global Cybersecurity Index[5] and measures five pillars for cybersecurity measured for the surveyed countries: five pillars: • legal measures; • technical measures; • organizational measures; • capacity development measures; • cooperation measures. Introduction to Cybersecurity Cybersecurity is a vital and rapidly evolving subject that specializes in shielding pc structures, networks, and records from numerous cyber threats and assaults. As our international turns into increasingly digitized and interconnected, the importance of cybersecurity has in no way been greater. In this advent to cybersecurity, we are able to explore the fundamental standards of cybersecurity, the importance of safeguarding virtual assets, and the risks posed through cyber threats. We'll delve into the distinctive forms of cyber assaults and the techniques employed through cyber criminals to take advantage of vulnerabilities. Moreover, we're going to talk the important thing additives of a robust cybersecurity method, which incorporates the use of superior technology, steady coding practices, and employee consciousness and education. Understanding the significance of cybersecurity in each private and expert settings is vital for making sure the protection of touchy data and maintaining virtual privacy. By the cease of this creation, you may have a foundational know-how of the cybersecurity panorama and the want for proactive measures to shield towards cyber threats. Whether you're an man or woman trying to safeguard your private data or a business owner searching for to defend essential belongings, the understanding won from this introduction will empower you to take proactive steps in fortifying your digital defenses against the ever-evolving threats inside the cyber realm. What is Cyber Securityhttps://cybersecuritycode.blogspot.com/2023/07/what-is-cyber-security-your-guide-to.html? Cybersecurity, often written as "cyber safety," is the practice of shielding computer systems, networks, gadgets, and information from virtual attacks and unauthorized access. It encompasses a range of technology, strategies, and practices designed to guard facts era (IT) systems and make sure their confidentiality, integrity, and availability. The primary intention of cybersecurity is to prevent cyber threats, such as hacking, facts breaches, malware, ransomware, phishing, and Distributed Denial of Service (DDoS) attacks. These threats can have intense outcomes, including monetary losses, recognition damage, and compromise of touchy data. Key elements of cybersecurity consist of: Information Security: Protecting sensitive records and facts from unauthorized get entry to, amendment, or disclosure. Network Security: Implementing measures to secure computer networks and save you unauthorized get entry to and records breaches. Endpoint Security: Protecting person gadgets, including computers, laptops, smartphones, and capsules, from malware and other threats. Application Security: Ensuring that software program and applications are unfastened from vulnerabilities that attackers ought to make the most. Cloud Security: Implementing security measures to defend facts and applications saved in cloud computing environments. Identity and Access Management (IAM): Controlling access to sources and records, ensuring that only legal users have suitable permissions Encryption: Using cryptographic techniques to encode information to protect it from unauthorized get entry to during transmission and storage. Incident Response: Developing a plan to reply successfully to cybersecurity incidents and mitigate their impact. Security Awareness and Training: Educating customers approximately cybersecurity fine practices and capability threats to sell a security-conscious lifestyle. Vulnerability Assessment and Penetration Testing: Identifying and addressing security weaknesses via ordinary trying out and evaluation. As the virtual panorama evolves, cyber threats hold to boost, making cybersecurity an ongoing and important challenge for people, agencies, governments, and businesses of all sizes. Adopting strong cybersecurity measures is important to guard touchy facts, keep business continuity, and protect against the ever-evolving cyber dangers in today's interconnected global. Personal Security- Safeguarding Your Digital Life https://cybersecuritycode.blogspot.com/2023/07/what-is-cyber-security-your-guide-to.html — Preceding unsigned comment added by Azizulsohel (talk • contribs) 18:05, 31 July 2023 (UTC) References[edit]References
|
- See the merge proposal that prompted this AfC, and the userfied draft. Tule-hog (talk) 19:03, 18 August 2024 (UTC)
Changing order and prioritising the general public
[edit]Hi everyone. I've recently been contracted to do some editing work on Wikipedia articles, and this is one of the articles my employers would like improving.
(TLDR; I'm trying to make the article easier and more accessible for the general public to help improve their own computer security, so some topics may be moved around.) Theobrad (talk) 11:49, 29 November 2023 (UTC)
- @Theobrad:, I see that you have declared your paid editing per WP:COI but, imo at least, it would be wise to refer here (and anywhere else you have done it) to that disclosure. Belt and braces. 𝕁𝕄𝔽 (talk) 22:05, 18 August 2024 (UTC)
- Hi there,
- Yes, I would agree. In hindsight I should have done this.
- I'm not paid to edit Wikipedia at the moment and am not working on this article currently. Theobrad (talk) 17:37, 23 August 2024 (UTC)
contracted edits
|
|---|
|
I've recently completely some research for my master's degree on making Wikipedia more easy to understand and readable. The research includes surveying over 500 members of the general public on their responses to climate change articles on Wikipedia. The results suggest that both readability scores on Wikipedia are detrimental to people's understanding of the information, and in some cases can lead to people mistrusting the information. I'm looking to implement some of these findings into this article - in short, improve the readability of certain sections. As well as readability, I also want to better prioritise information which suits the general public. Both the order of the article and the way advice is discussed on this article is slightly counterintuitive to aiding the general public on increasing their knowledge about computer security. Although computer security is a broad topic, topics that are within the realm of control or importance to the general public are mainly limited to protection and safety. This isn't prioritised in this article and is hidden amongst various subsections. Over the next few weeks I will test moving some things around in the article with the goal of making the article more productive and easy to navigate for the general public. I hope to maintain the overall tone and information of the article, but simultaneously make it more helpful for the general public. Please be free to comment on any of my edits if you believe it is changing the article in any way that you see unfit, and I would be more than happy to discuss your comments. Theobrad (talk) 11:49, 29 November 2023 (UTC) Removal of 'Importance of Cyber Security' section[edit]In the vein of condensing the article: keeping the information concise and in the right section, I believe this section (which is currently at the bottom of the article) may be slightly redundant following the rest of the information. With all respect to the author, as the section nicely summarises some of the points, unless it is placed high and condensed a bit as a kind of "summary" of issues, I don't think it should remain on its own at the bottom. Would love to hear people's thoughts.
Theobrad (talk) 12:46, 29 November 2023 (UTC)
|
Wiki Education assignment: Engineering in the 21st Century - Section 003
[edit]![]() This article is currently the subject of a Wiki Education Foundation-supported course assignment, between 19 August 2024 and 3 December 2024. Further details are available on the course page. Student editor(s): Kanialdhan (article contribs). Peer reviewers: GroupScientificDiscovery.
This article is currently the subject of a Wiki Education Foundation-supported course assignment, between 19 August 2024 and 3 December 2024. Further details are available on the course page. Student editor(s): Kanialdhan (article contribs). Peer reviewers: GroupScientificDiscovery.
— Assignment last updated by GroupScientificDiscovery (talk) 00:42, 21 October 2024 (UTC)
Wiki Education assignment: Research Process and Methodology - FA24 - Sect 200 - Thu
[edit]![]() This article is currently the subject of a Wiki Education Foundation-supported course assignment, between 5 September 2024 and 13 December 2024. Further details are available on the course page. Student editor(s): Sp7930 (article contribs).
This article is currently the subject of a Wiki Education Foundation-supported course assignment, between 5 September 2024 and 13 December 2024. Further details are available on the course page. Student editor(s): Sp7930 (article contribs).
— Assignment last updated by Sp7930 (talk) 04:21, 11 November 2024 (UTC)
- Wikipedia former featured articles
- Old requests for peer review
- C-Class level-4 vital articles
- Wikipedia level-4 vital articles in Technology
- C-Class vital articles in Technology
- C-Class Computing articles
- Top-importance Computing articles
- C-Class Computer networking articles
- High-importance Computer networking articles
- C-Class Computer networking articles of High-importance
- All Computer networking articles
- C-Class software articles
- High-importance software articles
- C-Class software articles of High-importance
- All Software articles
- C-Class Websites articles
- Low-importance Websites articles
- C-Class Websites articles of Low-importance
- All Websites articles
- C-Class Computer science articles
- Top-importance Computer science articles
- C-Class Computer hardware articles
- Low-importance Computer hardware articles
- C-Class Computer hardware articles of Low-importance
- C-Class Computer Security articles
- Top-importance Computer Security articles
- C-Class Computer Security articles of Top-importance
- All Computer Security articles
- All Computing articles
- C-Class Internet articles
- High-importance Internet articles
- WikiProject Internet articles
- C-Class Espionage articles
- High-importance Espionage articles










